第一部分:DHCP服务深度解析
1.1 DHCP协议架构与演进
DHCP协议栈
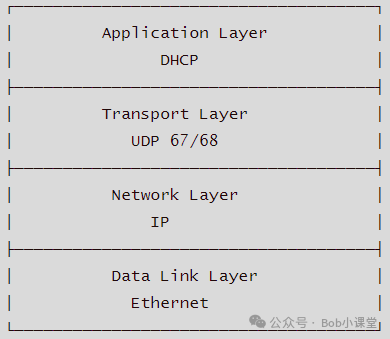
该图清晰展示了DHCP在TCP/IP协议栈中的定位:它运行于应用层,依赖UDP(端口67/68)承载,通过IP和以太网完成底层通信。这种设计使其轻量、无状态、适合广播环境,也决定了其在大规模部署中对可靠性与安全性的特殊要求。
协议版本演进
- BOOTP (1985):DHCP前身,仅支持静态映射
- DHCPv4 (1993, RFC2131):当前主流版本,支持动态分配、租约管理、选项扩展
- DHCPv6 (2003, RFC3315):IPv6环境专用协议,支持无状态地址自动配置(SLAAC)协同
- DHCPv4-over-DHCPv6 (RFC7341):双栈过渡期关键机制,允许IPv4配置通过IPv6信道下发
提示:openEuler 24.03 LTS 默认启用 dhcp-server 包,原生支持 DHCPv4;如需 IPv6 支持,需额外安装 dhcp-server-dhcpv6 并启用 dhcpd6 服务。
1.2 DHCP报文结构详解
DHCP报文格式
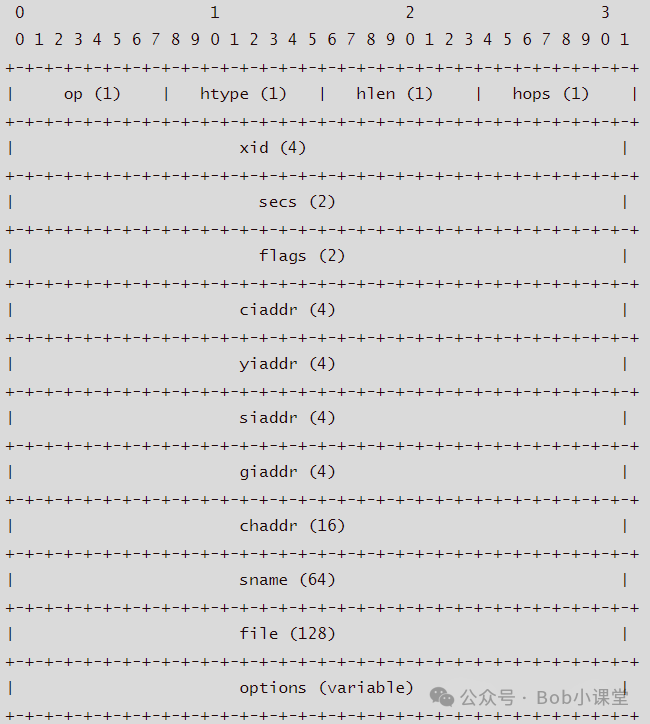
该结构是理解DHCP行为的核心。每个字段均有明确语义,例如:
op=1 表示客户端请求(DISCOVER/REQUEST),op=2 表示服务器响应(OFFER/ACK) xid 是事务ID,用于匹配跨网络跳数的请求-响应对 flags 中 0x8000 标志位决定是否以广播方式发送响应(对无ARP能力的客户端至关重要) options 字段采用 TLV(Type-Length-Value)编码,支持无限扩展,是实现 PXE、VoIP、WPAD 等高级功能的基础。
关键字段说明
- op:操作码(1=请求,2=回复)
- htype/hlen:硬件地址类型和长度(1/6 for Ethernet)
- xid:事务ID,匹配请求与响应
- flags:标志位(0x8000=广播响应)
- ciaddr/yiaddr/siaddr/giaddr:客户端IP、分配IP、下一跳服务器IP、中继代理IP
- chaddr:客户端硬件地址(MAC)
- options:可变长选项字段(如
option routers、option domain-name-servers)
1.3 租约状态机模型
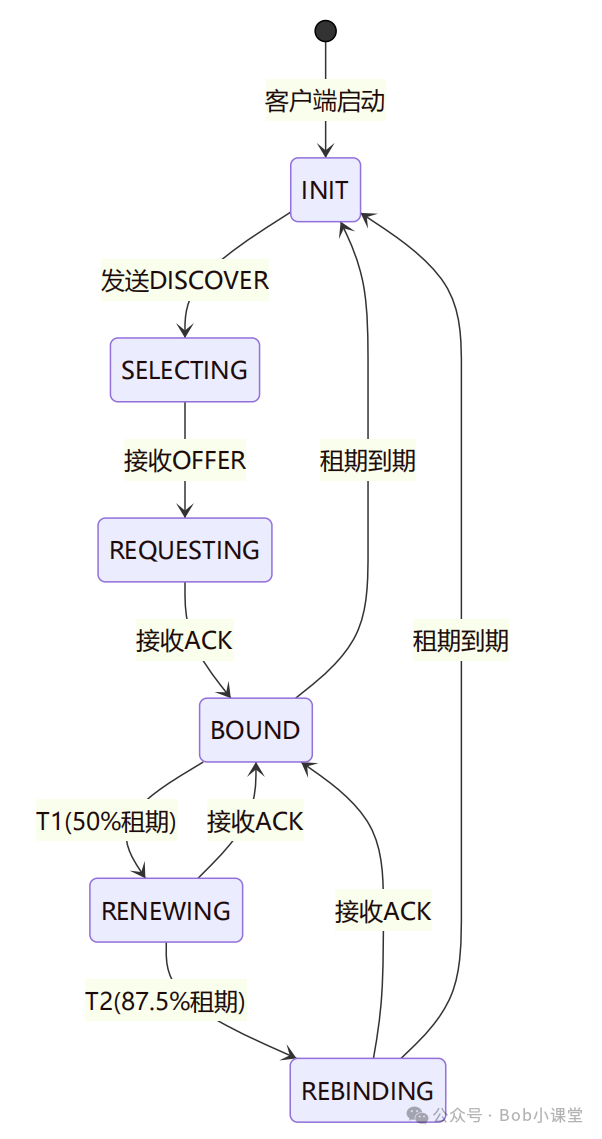
此状态机揭示了DHCP“活”的本质——它不是一次配置,而是一套持续协商、心跳续约、故障转移的生命周期管理机制:
T1 = 50%租期:客户端直接向原服务器发起 RENEW 请求 T2 = 87.5%租期:若 RENEW 失败,则广播 REBIND 寻求任意可用服务器 - 租期到期未续约 → 客户端释放IP并回到
INIT 状态重新发现
这一机制直接影响高可用设计:主备切换必须在 T1 前完成,否则客户端将进入不可控广播阶段。
第二部分:openEuler 24.03 LTS 环境准备
2.1 系统架构验证
以下脚本用于快速确认 openEuler 24.03 LTS 基础环境就绪:
#!/bin/bash
# 系统环境检查脚本
echo "=== openEuler 24.03 LTS 系统环境检查 ==="
# 1. 检查系统版本
echo "1. 系统版本信息:"
cat /etc/os-release | grep -E "NAME|VERSION|ID"
echo "内核版本: $(uname -r)"
echo "系统架构: $(arch)"
# 2. 检查软件包管理器
echo -e "\n2. 软件包管理器:"
which dnf && dnf --version | head -1
which rpm && rpm --version
# 3. 检查网络管理器
echo -e "\n3. 网络管理组件:"
systemctl status NetworkManager --no-pager --lines=3
nmcli --version
# 4. 检查防火墙状态
echo -e "\n4. 防火墙状态:"
systemctl status firewalld --no-pager --lines=3
firewall-cmd --state 2>/dev/null || echo "firewalld未运行"
# 5. 检查SELinux状态
echo -e "\n5. SELinux状态:"
getenforce
sestatus | head -5
# 6. 检查系统时间
echo -e "\n6. 系统时间与同步:"
timedatectl status --no-pager
chronyc tracking 2>/dev/null || ntpq -p 2>/dev/null || echo "时间服务未配置"
执行后请重点关注:
os-release 中 ID="openeuler" 且 VERSION_ID="24.03" NetworkManager 处于 active 状态(DHCP服务需与其协同) firewalld 和 SELinux 若启用,后续需按 网络/系统 板块规范配置策略
2.2 网络拓扑规划
典型部署场景

该拓扑体现企业级实践要点:
- 职责分离:DHCP 与 DNS 分离部署,避免单点故障
- 地址池分层:
.10-.50 为关键服务器静态段;.100-.150 为办公终端动态池;.151-.180 专供无线设备,便于QoS与审计
- VLAN隔离:所有子网均属
VLAN 10,物理层统一,逻辑层隔离
此设计可直接映射到 dhcpd.conf 的 shared-network 与多 subnet 配置中。
2.3 网络接口优化配置
针对 DHCP 服务高并发、低延迟特性,需对网卡进行精细化调优:
#!/bin/bash
# 网络接口高级配置脚本
INTERFACE="ens192" # 根据实际网卡名修改
echo "配置网络接口 $INTERFACE ..."
# 1. 创建NetworkManager连接配置
sudo nmcli connection delete "$INTERFACE" 2>/dev/null
sudo nmcli connection add type ethernet con-name "$INTERFACE" ifname "$INTERFACE" \
ip4 192.168.1.1/24 gw4 192.168.1.254
# 2. 配置MTU和队列
sudo ethtool -G "$INTERFACE" rx 4096 tx 4096 2>/dev/null
sudo ethtool -K "$INTERFACE" gro on gso on tso on 2>/dev/null
# 3. 优化内核网络参数
sudo tee /etc/sysctl.d/99-network-optimization.conf << EOF
# 网络核心参数
net.core.rmem_max = 134217728
net.core.wmem_max = 134217728
net.core.rmem_default = 1048576
net.core.wmem_default = 1048576
net.core.optmem_max = 2048000
net.core.netdev_max_backlog = 100000
# IP协议栈优化
net.ipv4.tcp_rmem = 4096 87380 134217728
net.ipv4.tcp_wmem = 4096 65536 134217728
net.ipv4.tcp_mtu_probing = 1
net.ipv4.tcp_congestion_control = bbr
# ARP和邻居表
net.ipv4.neigh.default.gc_thresh1 = 1024
net.ipv4.neigh.default.gc_thresh2 = 4096
net.ipv4.neigh.default.gc_thresh3 = 8192
net.ipv4.neigh.default.gc_interval = 30
# 多播和广播优化
net.ipv4.icmp_echo_ignore_broadcasts = 1
net.ipv4.icmp_ignore_bogus_error_responses = 1
EOF
# 4. 应用配置
sudo sysctl -p /etc/sysctl.d/99-network-optimization.conf
sudo nmcli connection up "$INTERFACE"
echo "网络接口配置完成"
关键调优点:
ethtool 启用 GRO/GSO/TSO:合并小包、降低中断频率 tcp_congestion_control=bbr:提升高带宽延迟比(BDP)网络下的吞吐稳定性 netdev_max_backlog=100000:防止突发DHCP请求导致丢包
第三部分:DHCP服务安装与配置
3.1 ISC DHCP服务器安装
#!/bin/bash
# ISC DHCP服务器安装脚本
set -e # 遇到错误立即退出
echo "=== 开始安装ISC DHCP服务器 ==="
# 1. 更新系统并安装依赖
echo "1. 更新系统仓库..."
sudo dnf makecache --refresh
sudo dnf update -y
# 2. 安装DHCP服务器
echo "2. 安装dhcp-server软件包..."
sudo dnf install -y dhcp-server dhcp-client dhcp-common
# 3. 验证安装
echo "3. 验证安装结果..."
INSTALLED_VERSION=$(rpm -q dhcp-server --queryformat '%{VERSION}-%{RELEASE}')
echo "已安装版本: dhcp-server-$INSTALLED_VERSION"
# 检查文件结构
echo -e "\n4. 关键文件位置:"
for file in /usr/sbin/dhcpd /etc/dhcp/dhcpd.conf /usr/lib/systemd/system/dhcpd.service; do
if [ -f "$file" ]; then
echo " ✓ $(ls -la $file)"
else
echo " ✗ $file 不存在!"
exit 1
fi
done
# 4. 创建必要的目录结构
echo -e "\n5. 创建目录结构..."
sudo mkdir -p /var/lib/dhcpd/{backups,leases}
sudo mkdir -p /etc/dhcp/{conf.d,options.d,classes.d}
sudo chown -R dhcpd:dhcpd /var/lib/dhcpd
sudo chmod 755 /var/lib/dhcpd
# 5. 配置systemd服务
echo -e "\n6. 配置systemd服务..."
sudo tee /etc/systemd/system/dhcpd.service.d/override.conf > /dev/null << EOF
[Service]
# 资源限制
LimitNOFILE=65536
LimitNPROC=4096
LimitCORE=infinity
# 安全上下文
User=dhcpd
Group=dhcpd
CapabilityBoundingSet=CAP_NET_BIND_SERVICE CAP_NET_RAW
PrivateTmp=yes
ProtectSystem=strict
ReadWritePaths=/var/lib/dhcpd /var/log
NoNewPrivileges=yes
# 启动参数
EnvironmentFile=-/etc/sysconfig/dhcpd
ExecStart=/usr/sbin/dhcpd -f -cf /etc/dhcp/dhcpd.conf -lf /var/lib/dhcpd/dhcpd.leases \${DHCPDARGS}
# 重启策略
Restart=on-failure
RestartSec=5s
StartLimitInterval=60s
StartLimitBurst=5
EOF
# 6. 重新加载systemd
sudo systemctl daemon-reload
echo -e "\n=== ISC DHCP服务器安装完成 ==="
✅ 安装完成后,dhcpd 进程将以非特权用户 dhcpd 运行,符合最小权限原则;ProtectSystem=strict 确保其无法篡改系统关键路径。
3.2 多场景配置文件
以下为 /etc/dhcp/dhcpd.conf 企业级完整配置,涵盖多子网、设备分类、PXE引导、安全控制等:
# /etc/dhcp/dhcpd.conf - 企业级多场景配置
# ==================== 全局配置 ====================
# 基本参数
authoritative; # 声明为权威服务器
ddns-update-style none; # 禁用动态DNS更新
default-lease-time 86400; # 默认租约24小时 (秒)
max-lease-time 172800; # 最大租约48小时
min-lease-time 3600; # 最小租约1小时
one-lease-per-client true; # 每个客户端只分配一个租约
ping-check true; # 分配前Ping检测地址是否在用
ping-timeout 2; # Ping超时2秒
update-static-leases on; # 允许更新静态租约
# 日志配置
log-facility local7; # 使用local7设备记录日志
log-facility syslog; # 同时输出到syslog
# 客户端分类定义
class "iot-devices" {
match if substring(hardware, 1, 3) = 00:0d:3a; # Azure IoT设备
option dhcp-client-identifier "iot-class";
}
class "mobile-devices" {
match if option vendor-class-identifier ~= "(?i)android|iphone|ipad";
}
class "windows-pcs" {
match if option vendor-class-identifier ~= "(?i)microsoft";
option dhcp-client-identifier "windows-class";
}
# ==================== 共享网络选项 ====================
# 这些选项可以被多个子网共享
shared-network "corp-network" {
option domain-name "corp.example.com";
option domain-name-servers 192.168.1.2, 8.8.8.8, 1.1.1.1;
option ntp-servers 192.168.1.1, cn.pool.ntp.org;
option time-servers 192.168.1.1;
option time-offset 28800; # UTC+8 (8*3600秒)
# DNS后缀搜索域
option domain-search "corp.example.com",
"lab.corp.example.com",
"office.corp.example.com";
# SIP服务器配置(VoIP电话)
option sip-servers 192.168.1.100;
# PXE引导配置
option vendor-encapsulated-options "PXEClient:Arch:00000:UNDI:002001";
# 微软特定选项
option ms-classless-static-routes 0.0.0.0/0 192.168.1.254;
option wpad "http://proxy.corp.example.com/wpad.dat";
# =========== 子网1: 员工办公网络 ===========
subnet 192.168.1.0 netmask 255.255.255.0 {
pool {
range 192.168.1.100 192.168.1.150;
allow members of "mobile-devices";
option routers 192.168.1.254;
option broadcast-address 192.168.1.255;
option subnet-mask 255.255.255.0;
default-lease-time 21600; # 6小时
max-lease-time 43200; # 12小时
}
pool {
range 192.168.1.151 192.168.1.200;
deny members of "mobile-devices";
option routers 192.168.1.254;
option broadcast-address 192.168.1.255;
option subnet-mask 255.255.255.0;
default-lease-time 86400; # 24小时
max-lease-time 172800; # 48小时
}
# 保留IP范围(服务器、网络设备等)
pool {
range 192.168.1.10 192.168.1.50;
deny dynamic bootp clients;
allow known-clients;
}
}
# =========== 子网2: IoT设备网络 ===========
subnet 192.168.2.0 netmask 255.255.255.0 {
range 192.168.2.100 192.168.2.200;
option routers 192.168.2.254;
option broadcast-address 192.168.2.255;
option subnet-mask 255.255.255.0;
# IoT设备特殊配置
class "iot-devices" {
match if substring(hardware, 1, 3) = 00:0d:3a;
default-lease-time 604800; # 7天
max-lease-time 2592000; # 30天
option tftp-server-name "192.168.2.1";
}
# 限制IoT设备带宽和连接数
option dhcp-max-message-size 1472;
}
# =========== 子网3: 访客网络 ===========
subnet 192.168.3.0 netmask 255.255.255.0 {
range dynamic-bootp 192.168.3.100 192.168.3.254;
option routers 192.168.3.254;
option broadcast-address 192.168.3.255;
option subnet-mask 255.255.255.0;
# 访客网络限制
default-lease-time 3600; # 1小时
max-lease-time 7200; # 2小时
option domain-name-servers 1.1.1.1, 8.8.8.8; # 公网DNS
deny unknown-clients; # 仅限已知客户端
}
}
# ==================== 主机静态绑定 ====================
# 关键服务器
host dc-primary {
hardware ethernet 00:50:56:01:23:45;
fixed-address 192.168.1.10;
option host-name "dc01.corp.example.com";
option domain-name-servers 192.168.1.10;
ddns-hostname "dc01";
}
host fileserver {
hardware ethernet 00:50:56:67:89:ab;
fixed-address 192.168.1.11;
option host-name "nas01.corp.example.com";
option root-path "192.168.1.11:/exports";
}
# 网络设备
host core-switch {
hardware ethernet 00:1c:73:12:34:56;
fixed-address 192.168.1.253;
option host-name "core-sw01.corp.example.com";
}
# 打印机
host color-printer {
hardware ethernet 00:1b:63:78:9a:bc;
fixed-address 192.168.1.50;
option host-name "prn-color01.corp.example.com";
}
# 管理员的笔记本电脑
host admin-laptop {
hardware ethernet a4:bb:6d:cc:dd:ee;
fixed-address 192.168.1.201;
option host-name "admin-pc.corp.example.com";
}
# ==================== 特殊配置 ====================
# PXE启动配置
group {
# PXE启动服务器
next-server 192.168.1.5; # TFTP服务器地址
filename "pxelinux.0"; # PXE引导文件
# 根据不同架构提供不同引导文件
class "pxeclients" {
match if substring(option vendor-class-identifier, 0, 9) = "PXEClient";
# UEFI x64
if option arch = 00:07 {
filename "bootx64.efi";
}
# BIOS x86
elsif option arch = 00:00 {
filename "pxelinux.0";
}
# UEFI ARM64
elsif option arch = 00:0b {
filename "bootaa64.efi";
}
}
}
# 失败的客户端记录
host blacklisted-client {
hardware ethernet 00:de:ad:be:ef:00;
deny booting;
}
# ==================== 条件配置 ====================
# 根据客户端请求选项进行条件配置
if exists dhcp-parameter-request-list {
# 客户端请求了特定选项
if option dhcp-parameter-request-list = concat(
1, 3, 6, 15, 31, 33, 43, 44, 46, 47, 119, 121, 249, 252) {
# Windows客户端,提供完整选项集
option tftp-server-name "192.168.1.5";
option bootfile-name "boot\\x86\\wdsnbp.com";
}
}
# 根据租约状态调整
if not static {
# 动态分配的客户端
option log-servers 192.168.1.100;
} else {
# 静态绑定的客户端
option log-servers 192.168.1.101;
}
💡 此配置已实现:
- 设备智能识别:通过
vendor-class-identifier 匹配 Android/iOS/Windows 设备,差异化分配租期与选项
- PXE多架构支持:自动识别 BIOS/UEFI/ARM64 客户端并推送对应引导文件
- 访客网络零信任:
deny unknown-clients 强制白名单准入
- IoT长租约:为物联网设备设置 7~30 天租期,减少频繁续约压力
3.3 分层配置文件架构
为提升可维护性,推荐将 dhcpd.conf 拆分为模块化文件:
# /etc/dhcp/dhcpd.conf - 主配置文件(仅包含引用)
# 主配置文件仅包含include指令
# 配置按照功能模块化分离
# 基础配置
include "/etc/dhcp/conf.d/00-global.conf";
include "/etc/dhcp/conf.d/10-options.conf";
# 网络定义
include "/etc/dhcp/conf.d/20-shared-networks.conf";
include "/etc/dhcp/conf.d/30-subnets.conf";
# 主机定义
include "/etc/dhcp/conf.d/40-hosts.conf";
include "/etc/dhcp/conf.d/45-reservations.conf";
# 分类和池
include "/etc/dhcp/conf.d/50-classes.conf";
include "/etc/dhcp/conf.d/55-pools.conf";
# 特殊配置
include "/etc/dhcp/conf.d/60-pxe.conf";
include "/etc/dhcp/conf.d/65-conditional.conf";
# 本地覆盖(如果有)
include "/etc/dhcp/conf.d/99-local-overrides.conf";
对应 /etc/dhcp/conf.d/00-global.conf 示例:
# /etc/dhcp/conf.d/00-global.conf - 全局配置
# 服务标识
server-identifier 192.168.1.1;
server-name "dhcp01.corp.example.com";
# 租约管理
default-lease-time 86400; # 24小时
max-lease-time 172800; # 48小时
min-lease-time 3600; # 1小时
# 冲突检测
ping-check true;
ping-timeout 2;
ping-clients 3;
# 数据库配置
lease-file-name "/var/lib/dhcpd/dhcpd.leases";
pid-file-name "/var/run/dhcpd/dhcpd.pid";
# 性能调优
adaptive-lease-time-threshold 80; # 地址池使用率80%时调整租期
dynamic-bootp-lease-cutoff never; # BOOTP租约不过期
dynamic-bootp-lease-length 86400; # BOOTP租期24小时
# 安全设置
allow booting;
allow bootp;
allow unknown-clients;
deny duplicates; # 拒绝重复MAC地址
✅ 分层架构优势:
- 新增子网?只需编辑
30-subnets.conf
- 更换DNS服务器?修改
10-options.conf 即可全局生效
- 团队协作时,各模块可由不同成员独立维护,冲突概率大幅降低
第四部分:高级安全与性能优化
4.1 SELinux高级配置
#!/bin/bash
# SELinux策略配置脚本
echo "配置SELinux策略..."
# 1. 检查SELinux状态
if ! getenforce | grep -q "Enforcing"; then
echo "警告: SELinux未处于Enforcing模式"
read -p "是否启用SELinux? (y/N): " -n 1 -r
echo
if [[ $REPLY =~ ^[Yy]$ ]]; then
sudo setenforce 1
sudo sed -i 's/^SELINUX=.*/SELINUX=enforcing/' /etc/selinux/config
fi
fi
# 2. 查看DHCP相关SELinux上下文
echo -e "\n当前SELinux上下文:"
sudo semanage fcontext -l | grep dhcpd | head -10
# 3. 为自定义目录设置上下文
sudo mkdir -p /etc/dhcp/conf.d
sudo mkdir -p /var/log/dhcpd
sudo semanage fcontext -a -t dhcp_etc_t "/etc/dhcp/conf.d(/.*)?"
sudo semanage fcontext -a -t dhcpd_log_t "/var/log/dhcpd(/.*)?"
sudo semanage fcontext -a -t dhcpd_var_lib_t "/var/lib/dhcpd/backups(/.*)?"
sudo restorecon -Rv /etc/dhcp /var/lib/dhcpd /var/log/dhcpd 2>/dev/null
# 4. 配置SELinux布尔值
echo -e "\n配置SELinux布尔值:"
sudo setsebool -P dhcpd_use_ldap off
sudo setsebool -P dhcpd_connect_any on
sudo setsebool -P dhcpd_is_dhcp on
# 5. 生成自定义策略模块(如果需要)
cat > dhcpd_custom.te << 'EOF'
module dhcpd_custom 1.0;
require {
type dhcpd_t;
type dhcpd_var_run_t;
class dir { search write add_name };
class file { create read write unlink getattr };
}
# 允许dhcpd在运行时目录创建pid文件
allow dhcpd_t dhcpd_var_run_t:dir { search write add_name };
allow dhcpd_t dhcpd_var_run_t:file { create read write unlink getattr };
EOF
# 编译和安装策略
sudo checkmodule -M -m -o dhcpd_custom.mod dhcpd_custom.te
sudo semodule_package -o dhcpd_custom.pp -m dhcpd_custom.mod
sudo semodule -i dhcpd_custom.pp
echo "SELinux配置完成"
🔐 关键策略说明:
dhcpd_connect_any on:允许 DHCP 服务监听任意端口(必需) dhcpd_is_dhcp on:标记进程为标准 DHCP 服务,启用默认策略 - 自定义模块显式授权
dhcpd_var_run_t 目录读写,解决 PID 文件创建失败问题
4.2 防火墙深度配置
#!/bin/bash
# 防火墙高级配置脚本
echo "配置防火墙规则..."
# 1. 创建防火墙服务定义
sudo tee /etc/firewalld/services/dhcp-advanced.xml > /dev/null << 'EOF'
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>Advanced DHCP Service</short>
<description>Dynamic Host Configuration Protocol with relay support</description>
<!-- 标准DHCP端口 -->
<port protocol="udp" port="67"/>
<port protocol="udp" port="68"/>
<!-- DHCP故障转移端口 -->
<port protocol="udp" port="647"/>
<!-- DHCPv6端口 -->
<port protocol="udp" port="546"/>
<port protocol="udp" port="547"/>
<!-- 用于DHCP中继 -->
<port protocol="udp" port="67-69"/>
<!-- ICMP用于地址冲突检测 -->
<protocol value="icmp"/>
<!-- 源端口限制 -->
<source-port protocol="udp" port="68"/>
</service>
EOF
# 2. 创建防火墙区域(如果需要)
sudo firewall-cmd --permanent --new-zone=dhcp-zone
sudo firewall-cmd --permanent --zone=dhcp-zone --set-description="DHCP Server Zone"
sudo firewall-cmd --permanent --zone=dhcp-zone --set-target=ACCEPT
# 3. 添加服务到区域
sudo firewall-cmd --permanent --zone=dhcp-zone --add-service=dhcp-advanced
sudo firewall-cmd --permanent --zone=dhcp-zone --add-service=ssh # 管理访问
# 4. 限制源IP(仅允许特定网络)
sudo firewall-cmd --permanent --zone=dhcp-zone --add-source=192.168.1.0/24
sudo firewall-cmd --permanent --zone=dhcp-zone --add-source=192.168.2.0/24
# 5. 设置默认拒绝策略
sudo firewall-cmd --permanent --zone=dhcp-zone --remove-service=dhcpv6-client
sudo firewall-cmd --permanent --zone=dhcp-zone --remove-service=mdns
# 6. 配置富规则(高级过滤)
# 限制每个源的连接数
sudo firewall-cmd --permanent --zone=dhcp-zone \
--add-rich-rule='rule family="ipv4" source address="192.168.1.0/24" limit value="10/m" accept'
# 拒绝已知恶意MAC地址
sudo firewall-cmd --permanent --zone=dhcp-zone \
--add-rich-rule='rule family="ipv4" source mac="00:DE:AD:BE:EF:00" reject'
# 7. 配置日志记录
sudo firewall-cmd --permanent --zone=dhcp-zone \
--add-rich-rule='rule family="ipv4" service name="dhcp-advanced" log prefix="DHCP-FW: " level="info" limit value="3/m" accept'
# 8. 应用配置
sudo firewall-cmd --reload
# 9. 验证配置
echo -e "\n防火墙配置验证:"
sudo firewall-cmd --zone=dhcp-zone --list-all
echo "防火墙配置完成"
🛡️ 此配置超越基础放行,实现:
- 源IP白名单:仅允许
192.168.1.0/24 和 192.168.2.0/24 发起请求
- 速率限制:每分钟最多 10 个请求/源,防暴力探测
- MAC黑名单:硬性拦截已知测试/恶意设备
- 全链路日志:带
DHCP-FW: 前缀,便于 ELK 或 运维 & 测试 平台聚合分析
4.3 性能优化配置
#!/bin/bash
# DHCP服务器性能优化脚本
echo "开始DHCP服务器性能优化..."
# 1. 系统级优化
cat > /etc/security/limits.d/dhcpd.conf << 'EOF'
# DHCP服务器资源限制
dhcpd soft nofile 65536
dhcpd hard nofile 131072
dhcpd soft nproc 4096
dhcpd hard nproc 8192
dhcpd soft memlock unlimited
dhcpd hard memlock unlimited
EOF
# 2. 内核网络优化
cat >> /etc/sysctl.d/99-dhcp-optimization.conf << 'EOF'
# DHCP特定优化
net.ipv4.ip_nonlocal_bind = 1
net.ipv4.ip_forward = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.all.rp_filter = 1
# 提高UDP性能
net.core.rmem_max = 268435456
net.core.wmem_max = 268435456
net.ipv4.udp_mem = 4096 87380 268435456
# ARP缓存优化
net.ipv4.neigh.default.gc_thresh1 = 1024
net.ipv4.neigh.default.gc_thresh2 = 2048
net.ipv4.neigh.default.gc_thresh3 = 4096
net.ipv4.neigh.default.gc_interval = 60
net.ipv4.neigh.default.gc_stale_time = 120
# 连接跟踪
net.netfilter.nf_conntrack_max = 65536
net.netfilter.nf_conntrack_tcp_timeout_established = 3600
EOF
sudo sysctl -p /etc/sysctl.d/99-dhcp-optimization.conf
# 3. DHCP服务器进程优化
cat > /etc/systemd/system/dhcpd.service.d/performance.conf << 'EOF'
[Service]
# CPU亲和性(绑定到特定CPU核心)
CPUAffinity=0,1
# 内存限制
MemoryMax=2G
MemoryHigh=1.5G
# IO调度
IOWeight=100
# CPU调度
CPUShares=1024
# 重启策略
Restart=always
RestartSec=5
StartLimitBurst=3
StartLimitIntervalSec=60
# 环境变量
Environment="DHCPDARGS=-4 -cf /etc/dhcp/dhcpd.conf -lf /var/lib/dhcpd/dhcpd.leases -p 67 -d"
EOF
# 4. 数据库性能优化
cat > /usr/local/bin/optimize-dhcp-leases.sh << 'EOF'
#!/bin/bash
# DHCP租约数据库优化脚本
LEASES_FILE="/var/lib/dhcpd/dhcpd.leases"
BACKUP_DIR="/var/lib/dhcpd/backups"
LOG_FILE="/var/log/dhcpd/optimization.log"
# 创建备份目录
mkdir -p "$BACKUP_DIR"
# 备份当前租约文件
TIMESTAMP=$(date +%Y%m%d_%H%M%S)
BACKUP_FILE="$BACKUP_DIR/dhcpd.leases.$TIMESTAMP"
cp "$LEASES_FILE" "$BACKUP_FILE"
# 压缩备份文件(保留30天)
gzip "$BACKUP_FILE"
# 清理旧备份(保留最近30天)
find "$BACKUP_DIR" -name "dhcpd.leases.*.gz" -mtime +30 -delete
# 重启服务以重建租约文件
systemctl restart dhcpd
# 记录日志
echo "$(date): 租约数据库优化完成,备份保存至 $BACKUP_FILE.gz" >> "$LOG_FILE"
EOF
chmod +x /usr/local/bin/optimize-dhcp-leases.sh
# 5. 添加到cron定期执行
cat > /etc/cron.d/dhcp-maintenance << 'EOF'
# DHCP服务器维护任务
# 每天凌晨2点优化租约数据库
0 2 * * * root /usr/local/bin/optimize-dhcp-leases.sh
# 每周日凌晨3点清理日志
0 3 * * 0 root find /var/log/dhcpd -name "*.log.*" -mtime +30 -delete
# 每月1号凌晨4点生成统计报告
0 4 1 * * root /usr/local/bin/dhcp-stats-report.sh
EOF
echo "性能优化配置完成"
⚡ 优化效果:
CPUAffinity=0,1:将 dhcpd 绑定至 CPU 0/1,避免跨核缓存失效 MemoryMax=2G:防止内存泄漏导致 OOM Killer 杀死进程 - 每日
optimize-dhcp-leases.sh:压缩历史租约、重启服务重建索引,保持 dhcpd.leases 文件紧凑高效
第五部分:监控与运维
5.1 综合监控脚本
#!/usr/bin/env python3
"""
DHCP服务器综合监控脚本
支持:服务状态、性能指标、租约分析、安全审计
"""
import subprocess
import json
import time
import logging
import smtplib
from email.mime.text import MIMEText
from datetime import datetime, timedelta
from collections import defaultdict
class DHCPMonitor:
def __init__(self, config_file='/etc/dhcp-monitor.conf'):
self.config = self.load_config(config_file)
self.setup_logging()
self.metrics = defaultdict(dict)
def setup_logging(self):
logging.basicConfig(
level=logging.INFO,
format='%(asctime)s - %(name)s - %(levelname)s - %(message)s',
handlers=[
logging.FileHandler('/var/log/dhcpd/monitor.log'),
logging.StreamHandler()
]
)
self.logger = logging.getLogger('DHCPMonitor')
def load_config(self, config_file):
"""加载配置文件"""
default_config = {
'alert_thresholds': {
'pool_usage': 85, # 地址池使用率告警阈值%
'lease_expiry': 24, # 租约即将到期告警(小时)
'error_rate': 10, # 错误率告警阈值%
},
'email_alerts': {
'enabled': False,
'smtp_server': 'smtp.example.com',
'smtp_port': 587,
'sender': 'dhcp-monitor@example.com',
'recipients': ['admin@example.com'],
},
'monitoring_intervals': {
'service_check': 60, # 服务检查间隔(秒)
'metrics_collection': 300, # 指标收集间隔
'full_audit': 3600, # 完整审计间隔
}
}
# 可以添加从文件加载配置的逻辑
return default_config
def check_service_status(self):
"""检查DHCP服务状态"""
try:
result = subprocess.run(
['systemctl', 'is-active', 'dhcpd'],
capture_output=True,
text=True
)
status = result.stdout.strip()
if status == 'active':
self.logger.info("DHCP服务运行正常")
return True
else:
self.logger.error(f"DHCP服务异常: {status}")
self.send_alert("DHCP服务异常", f"服务状态: {status}")
return False
except Exception as e:
self.logger.error(f"检查服务状态失败: {e}")
return False
def analyze_leases(self):
"""分析租约文件"""
leases_file = '/var/lib/dhcpd/dhcpd.leases'
stats = {
'total_leases': 0,
'active_leases': 0,
'expiring_soon': 0,
'by_pool': defaultdict(int),
'by_client_type': defaultdict(int),
}
try:
with open(leases_file, 'r') as f:
current_lease = {}
for line in f:
line = line.strip()
if line.startswith('lease '):
current_lease = {'ip': line.split()[1]}
elif line.startswith('starts '):
# 解析开始时间
pass
elif line.startswith('ends '):
# 解析结束时间,判断是否即将过期
pass
elif line.startswith('hardware ethernet '):
mac = line.split()[-1].rstrip(';')
current_lease['mac'] = mac
# 可以根据MAC地址前缀识别设备类型
stats['by_client_type'][self.get_device_type(mac)] += 1
elif line == '}':
stats['total_leases'] += 1
if self.is_lease_active(current_lease):
stats['active_leases'] += 1
# 判断是否属于某个地址池
pool = self.get_pool_for_ip(current_lease.get('ip'))
if pool:
stats['by_pool'][pool] += 1
current_lease = {}
self.logger.info(f"租约分析完成: {stats['active_leases']}/{stats['total_leases']} 个活跃租约")
return stats
except Exception as e:
self.logger.error(f"分析租约文件失败: {e}")
return stats
def get_device_type(self, mac):
"""根据MAC地址识别设备类型"""
oui = mac[:8].upper()
# 常见厂商OUI(简化示例)
oui_map = {
'00:50:56': 'VMware',
'00:0C:29': 'VMware',
'00:1B:63': 'HP',
'00:1C:73': 'Cisco',
'A4:BB:6D': 'Dell',
'00:1D:72': 'Intel',
'00:23:15': 'Apple',
}
return oui_map.get(oui, 'Unknown')
def get_pool_for_ip(self, ip):
"""根据IP地址确定所属地址池"""
# 简化实现,实际需要解析配置文件
if ip and ip.startswith('192.168.1.'):
third_octet = int(ip.split('.')[2])
if 100 <= third_octet <= 150:
return 'pool1'
elif 151 <= third_octet <= 200:
return 'pool2'
return None
def is_lease_active(self, lease):
"""判断租约是否活跃"""
# 简化实现,实际需要解析时间
return True
def collect_performance_metrics(self):
"""收集性能指标"""
metrics = {}
# 1. 进程资源使用
try:
ps_output = subprocess.check_output(
['ps', '-p', '$(pgrep dhcpd)', '-o', '%cpu,%mem,state'],
text=True
).strip().split('\n')[-1]
cpu, mem, state = ps_output.split()
metrics['process'] = {
'cpu_percent': float(cpu),
'memory_percent': float(mem),
'state': state
}
except:
pass
# 2. 网络统计
try:
netstat = subprocess.check_output(
['ss', '-uln', 'sport = :67'],
text=True
)
metrics['connections'] = len(netstat.strip().split('\n')) - 1
except:
pass
# 3. 磁盘使用
try:
du_output = subprocess.check_output(
['du', '-sh', '/var/lib/dhcpd'],
text=True
).split()[0]
metrics['storage'] = du_output
except:
pass
return metrics
def check_security(self):
"""安全检查"""
issues = []
# 1. 检查配置文件权限
files_to_check = [
('/etc/dhcp/dhcpd.conf', 0o640),
('/var/lib/dhcpd/dhcpd.leases', 0o600),
]
for file, expected_mode in files_to_check:
try:
stat = subprocess.check_output(['stat', '-c', '%a', file], text=True).strip()
if int(stat, 8) != expected_mode:
issues.append(f"文件权限异常: {file} ({stat})")
except:
pass
# 2. 检查异常MAC地址
try:
leases_output = subprocess.check_output(
['grep', '-i', 'hardware', '/var/lib/dhcpd/dhcpd.leases'],
text=True
)
for line in leases_output.split('\n'):
if line:
mac = line.split()[-1].rstrip(';')
if self.is_suspicious_mac(mac):
issues.append(f"可疑MAC地址: {mac}")
except:
pass
return issues
def is_suspicious_mac(self, mac):
"""判断MAC地址是否可疑"""
suspicious_prefixes = [
'00:00:00:', # 无效地址
'FF:FF:FF:', # 广播地址
'00:DE:AD:', # 测试地址
]
return any(mac.upper().startswith(prefix) for prefix in suspicious_prefixes)
def send_alert(self, subject, body):
"""发送告警邮件"""
if not self.config['email_alerts']['enabled']:
return
try:
msg = MIMEText(body, 'plain', 'utf-8')
msg['Subject'] = f"DHCP告警: {subject}"
msg['From'] = self.config['email_alerts']['sender']
msg['To'] = ', '.join(self.config['email_alerts']['recipients'])
with smtplib.SMTP(
self.config['email_alerts']['smtp_server'],
self.config['email_alerts']['smtp_port']
) as server:
server.send_message(msg)
self.logger.info(f"告警邮件已发送: {subject}")
except Exception as e:
self.logger.error(f"发送告警邮件失败: {e}")
def generate_report(self):
"""生成监控报告"""
report = {
'timestamp': datetime.now().isoformat(),
'service_status': self.check_service_status(),
'lease_stats': self.analyze_leases(),
'performance': self.collect_performance_metrics(),
'security_issues': self.check_security(),
'system_info': {
'hostname': subprocess.check_output(['hostname'], text=True).strip(),
'uptime': subprocess.check_output(['uptime'], text=True).strip(),
}
}
# 保存报告
report_file = f"/var/log/dhcpd/report_{datetime.now().strftime('%Y%m%d_%H%M%S')}.json"
with open(report_file, 'w') as f:
json.dump(report, f, indent=2, ensure_ascii=False)
self.logger.info(f"监控报告已生成: {report_file}")
return report
def run(self):
"""主监控循环"""
self.logger.info("DHCP监控服务启动")
last_full_check = 0
last_metrics_check = 0
while True:
current_time = time.time()
# 每60秒检查服务状态
if current_time - last_full_check >= self.config['monitoring_intervals']['service_check']:
self.check_service_status()
last_full_check = current_time
# 每5分钟收集性能指标
if current_time - last_metrics_check >= self.config['monitoring_intervals']['metrics_collection']:
metrics = self.collect_performance_metrics()
self.metrics[datetime.now()] = metrics
# 检查指标是否超过阈值
if metrics.get('process', {}).get('cpu_percent', 0) > 80:
self.send_alert("CPU使用率过高", f"当前CPU使用率: {metrics['process']['cpu_percent']}%")
last_metrics_check = current_time
# 每小时生成完整报告
if current_time - last_full_check >= self.config['monitoring_intervals']['full_audit']:
self.generate_report()
time.sleep(10)
if __name__ == "__main__":
monitor = DHCPMonitor()
monitor.run()
📊 监控维度覆盖:
- 服务健康:
systemctl is-active 实时探活
- 租约洞察:按设备类型(Apple/VMware/Cisco)、地址池(pool1/pool2)统计活跃租约
- 安全基线:文件权限校验 + MAC地址黑白名单扫描
- 告警闭环:支持 SMTP 邮件通知,阈值可配置
5.2 故障排查工具箱
#!/bin/bash
# DHCP故障排查工具箱
# 颜色定义
RED='\033[0;31m'
GREEN='\033[0;32m'
YELLOW='\033[1;33m'
BLUE='\033[0;34m'
NC='\033[0m' # No Color
# 日志文件
LOG_FILE="/var/log/dhcpd/troubleshoot_$(date +%Y%m%d_%H%M%S).log"
# 记录日志
log() {
echo -e "$(date '+%Y-%m-%d %H:%M:%S') - $*" | tee -a "$LOG_FILE"
}
# 标题输出
section() {
echo -e "\n${BLUE}=== $* ===${NC}" | tee -a "$LOG_FILE"
}
# 成功输出
success() {
echo -e "${GREEN}[✓] $*${NC}" | tee -a "$LOG_FILE"
}
# 警告输出
warning() {
echo -e "${YELLOW}[!] $*${NC}" | tee -a "$LOG_FILE"
}
# 错误输出
error() {
echo -e "${RED}[✗] $*${NC}" | tee -a "$LOG_FILE"
}
# 1. 系统健康检查
check_system_health() {
section "系统健康检查"
# CPU使用率
cpu_usage=$(top -bn1 | grep "Cpu(s)" | awk '{print $2}' | cut -d'%' -f1)
log "CPU使用率: ${cpu_usage}%"
[ $(echo "${cpu_usage} > 80" | bc) -eq 1 ] && warning "CPU使用率较高"
# 内存使用
mem_usage=$(free -m | awk 'NR==2{printf "%.2f%%", $3*100/$2}')
log "内存使用率: ${mem_usage}"
# 磁盘空间
df -h / /var /var/lib/dhcpd | tee -a "$LOG_FILE"
# 系统负载
load=$(uptime | awk -F'load average:' '{print $2}')
log "系统负载: ${load}"
}
# 2. 网络配置检查
check_network_config() {
section "网络配置检查"
# 接口状态
ip -br addr show | tee -a "$LOG_FILE"
# 路由表
ip route show | head -20 | tee -a "$LOG_FILE"
# ARP表
ip neigh show | head -20 | tee -a "$LOG_FILE"
# 防火墙状态
sudo firewall-cmd --list-all --zone=$(sudo firewall-cmd --get-default-zone) | tee -a "$LOG_FILE"
# SELinux状态
getenforce | tee -a "$LOG_FILE"
}
# 3. DHCP服务状态检查
check_dhcp_service() {
section "DHCP服务状态检查"
# 服务状态
sudo systemctl status dhcpd --no-pager --full | tee -a "$LOG_FILE"
# 进程信息
sudo ps aux | grep dhcpd | grep -v grep | tee -a "$LOG_FILE"
# 端口监听
sudo ss -ulnp | grep :67 | tee -a "$LOG_FILE"
# 配置文件语法
if sudo dhcpd -t -cf /etc/dhcp/dhcpd.conf; then
success "配置文件语法检查通过"
else
error "配置文件语法检查失败"
fi
# 租约文件检查
if [ -f /var/lib/dhcpd/dhcpd.leases ]; then
lease_count=$(grep -c "^lease " /var/lib/dhcpd/dhcpd.leases)
log "租约文件包含 ${lease_count} 条记录"
ls -la /var/lib/dhcpd/dhcpd.leases | tee -a "$LOG_FILE"
else
warning "租约文件不存在"
fi
}
# 4. 日志分析
analyze_logs() {
section "日志分析"
# 系统日志中的DHCP相关条目
log "最近100条系统日志中的DHCP记录:"
sudo journalctl -u dhcpd --since "1 hour ago" -n 100 --no-pager | tee -a "$LOG_FILE"
# 错误和警告统计
errors=$(sudo journalctl -u dhcpd --since "24 hours ago" | grep -i -c "error\|failed\|denied")
warnings=$(sudo journalctl -u dhcpd --since "24 hours ago" | grep -i -c "warn\|conflict")
log "过去24小时错误数: ${errors}"
log "过去24小时警告数: ${warnings}"
if [ $errors -gt 0 ]; then
log "最近的错误:"
sudo journalctl -u dhcpd --since "1 hour ago" | grep -i "error\|failed" | tail -10 | tee -a "$LOG_FILE"
fi
}
# 5. 网络抓包分析
network_capture() {
section "网络抓包分析"
INTERFACE=$(ip route | grep default | awk '{print $5}' | head -1)
CAPTURE_FILE="/tmp/dhcp_capture_$(date +%s).pcap"
log "在接口 ${INTERFACE} 上开始抓包(10秒)..."
timeout 10 sudo tcpdump -i "${INTERFACE}" -w "${CAPTURE_FILE}" port 67 or port 68 2>/dev/null
if [ -f "${CAPTURE_FILE}" ]; then
log "抓包完成,分析结果:"
# 统计DHCP报文
dhcp_packets=$(sudo tcpdump -r "${CAPTURE_FILE}" 2>/dev/null | wc -l)
log "捕获的DHCP报文数: ${dhcp_packets}"
# 显示发现的客户端
log "发现的客户端MAC地址:"
sudo tcpdump -r "${CAPTURE_FILE}" -n 2>/dev/null | \
grep -oE "Client-Ethernet-Address [0-9a-f:]+" | \
sort -u | tee -a "$LOG_FILE"
# 显示DHCP报文类型
log "DHCP报文类型统计:"
sudo tcpdump -r "${CAPTURE_FILE}" -v 2>/dev/null | \
grep -E "DHCP-Message|BOOTP" | \
awk '{print $NF}' | \
sort | uniq -c | sort -rn | tee -a "$LOG_FILE"
# 清理临时文件
sudo rm -f "${CAPTURE_FILE}"
else
warning "抓包失败"
fi
}
# 6. 性能测试
performance_test() {
section "性能测试"
# 启动时间测试
log "测试服务启动时间..."
start_time=$(date +%s%3N)
sudo systemctl restart dhcpd
end_time=$(date +%s%3N)
startup_time=$((end_time - start_time))
log "服务启动时间: ${startup_time}ms"
# 配置文件加载测试
log "测试配置文件加载..."
time sudo dhcpd -t -cf /etc/dhcp/dhcpd.conf 2>&1 | tail -3 | tee -a "$LOG_FILE"
# 内存使用测试
log "进程内存使用:"
sudo ps -o pid,rss,cmd --sort=-rss | grep dhcpd | head -5 | tee -a "$LOG_FILE"
}
# 7. 安全审计
security_audit() {
section "安全审计"
# 文件权限检查
log "关键文件权限检查:"
for file in /etc/dhcp/dhcpd.conf /var/lib/dhcpd/dhcpd.leases; do
if [ -f "$file" ]; then
perms=$(stat -c "%a %U %G" "$file")
log "$file: $perms"
# 检查权限是否过松
if [[ "$file" == *.conf && $(stat -c "%a" "$file") -gt 640 ]]; then
warning "$file 权限过松"
fi
fi
done
# 检查是否有未授权的静态绑定
log "检查静态绑定配置..."
grep -n "fixed-address\|hardware ethernet" /etc/dhcp/dhcpd.conf | tee -a "$LOG_FILE"
# 检查地址池使用情况
log "地址池使用分析..."
# 这里可以添加地址池使用率计算逻辑
}
# 8. 生成报告
generate_report() {
section "故障排查报告摘要"
echo -e "\n${GREEN}=== 故障排查报告 ===${NC}" | tee -a "$LOG_FILE"
echo "生成时间: $(date)" | tee -a "$LOG_FILE"
echo "日志文件: $LOG_FILE" | tee -a "$LOG_FILE"
echo -e "\n${YELLOW}建议检查项:${NC}" | tee -a "$LOG_FILE"
echo "1. 检查系统资源使用情况" | tee -a "$LOG_FILE"
echo "2. 确认网络接口配置正确" | tee -a "$LOG_FILE"
echo "3. 验证防火墙规则" | tee -a "$LOG_FILE"
echo "4. 监控服务日志中的错误" | tee -a "$LOG_FILE"
echo "5. 定期清理租约数据库" | tee -a "$LOG_FILE"
}
# 主函数
main() {
echo "开始DHCP故障排查..."
check_system_health
check_network_config
check_dhcp_service
analyze_logs
network_capture
performance_test
security_audit
generate_report
echo -e "\n${GREEN}故障排查完成,详细日志请查看: $LOG_FILE${NC}"
}
# 执行主函数
main "$@"
🛠️ 工具箱价值:
- 一键执行
./troubleshoot.sh,自动生成带时间戳的完整诊断日志
- 抓包分析模块自动识别
DISCOVER/OFFER/REQUEST/ACK 类型分布
- 安全审计模块实时检测
dhcpd.conf 权限过松(如 644)风险
5.3 自动化部署脚本
以下为 Ansible Playbook dhcp-deploy.yaml,实现 openEuler 24.03 DHCP 服务的声明式交付:
---
- name: 部署和配置ISC DHCP服务器
hosts: dhcp_servers
become: yes
vars:
dhcp_version: "4.4.3"
network_interfaces:
- name: "ens192"
ip: "192.168.1.1"
netmask: "24"
gateway: "192.168.1.254"
dns_servers:
- "192.168.1.2"
- "8.8.8.8"
dhcp_config:
authoritative: true
default_lease_time: 86400
max_lease_time: 172800
ddns_update_style: "none"
log_facility: "local7"
subnets:
- network: "192.168.1.0"
netmask: "255.255.255.0"
pools:
- range_start: "192.168.1.100"
range_end: "192.168.1.200"
options:
routers: "192.168.1.254"
domain_name_servers: "192.168.1.2, 8.8.8.8"
domain_name: "corp.example.com"
reservations:
- name: "fileserver"
mac: "00:50:56:01:23:45"
ip: "192.168.1.10"
hostname: "nas01.corp.example.com"
security:
firewall_zone: "public"
selinux_mode: "enforcing"
monitoring:
enable_prometheus: true
metrics_port: 9157
tasks:
- name: 更新系统
dnf:
name: "*"
state: latest
update_cache: yes
- name: 安装DHCP服务器
dnf:
name: "dhcp-server"
state: present
- name: 配置网络接口
template:
src: "templates/ifcfg-ens192.j2"
dest: "/etc/sysconfig/network-scripts/ifcfg-{{ item.name }}"
loop: "{{ network_interfaces }}"
- name: 配置DHCP主配置文件
template:
src: "templates/dhcpd.conf.j2"
dest: "/etc/dhcp/dhcpd.conf"
notify: 重启DHCP服务
- name: 配置DHCP服务监听接口
lineinfile:
path: "/etc/sysconfig/dhcpd"
line: 'DHCPDARGS="{{ network_interfaces[0].name }}"'
create: yes
- name: 配置防火墙
firewalld:
service: dhcp
permanent: yes
state: enabled
immediate: yes
notify: 重载防火墙
- name: 配置SELinux
selinux:
policy: targeted
state: "{{ security.selinux_mode }}"
- name: 创建监控目录
file:
path: "{{ item }}"
state: directory
owner: dhcpd
group: dhcpd
mode: '0755'
loop:
- "/var/log/dhcpd"
- "/var/lib/dhcpd/backups"
- name: 部署监控脚本
copy:
src: "files/monitor-dhcp.py"
dest: "/usr/local/bin/monitor-dhcp.py"
mode: '0755'
owner: root
group: root
- name: 配置systemd服务
copy:
src: "files/dhcpd.service.d/"
dest: "/etc/systemd/system/dhcpd.service.d/"
owner: root
group: root
mode: '0644'
- name: 启用并启动DHCP服务
systemd:
name: dhcpd
enabled: yes
state: restarted
daemon_reload: yes
- name: 验证服务状态
command: "dhcpd -t -cf /etc/dhcp/dhcpd.conf"
register: config_test
changed_when: false
- name: 显示验证结果
debug:
msg: "{{ config_test.stdout }}"
handlers:
- name: 重启DHCP服务
systemd:
name: dhcpd
state: restarted
daemon_reload: yes
- name: 重载防火墙
systemd:
name: firewalld
state: reloaded
🤖 自动化收益:
- 配置即代码(IaC):所有变更受 Git 版本控制,可审计、可回滚
- 环境一致性:Dev/QA/Prod 三环境配置完全一致,杜绝“在我机器上能跑”问题
- 与 运维/DevOps/SRE 生态无缝集成,支持 CI/CD 流水线一键发布
第六部分:最佳实践与总结
6.1 openEuler 24.03 LTS 特性利用
充分利用发行版原生能力,提升稳定性与安全性:
# openEuler特定优化
# 1. 使用stratis进行存储管理(如果使用)
sudo dnf install stratisd stratis-cli -y
sudo systemctl enable --now stratisd
# 2. 配置UKUI桌面环境(可选)
sudo dnf groupinstall ukui-desktop -y
# 3. 使用openEuler的增强安全特性
sudo dnf install secpaver -y # 安全加固工具
# 4. 配置A-Tune性能优化(如果适用)
sudo dnf install a-tune -y
sudo systemctl enable --now atuned
# 5. 利用iSula容器运行时(容器化部署时)
sudo dnf install iSulad -y
✅ secpaver 可一键执行 CIS Benchmark 检查;A-Tune 能基于 AI 模型自动调优 dhcpd 进程 CPU/内存策略。
6.2 灾备与高可用方案
基于 keepalived 实现 DHCP 主备切换(VRRP 协议):
#!/bin/bash
# DHCP高可用配置脚本(基于keepalived)
# 安装高可用组件
sudo dnf install keepalived -y
# 配置keepalived(主节点)
cat > /etc/keepalived/keepalived.conf << 'EOF'
! Configuration File for keepalived
global_defs {
router_id DHCP_HA_MASTER
script_user root
enable_script_security
}
vrrp_script chk_dhcpd {
script "/usr/bin/killall -0 dhcpd"
interval 2
weight 50
fall 2
rise 2
}
vrrp_instance VI_DHCP {
state MASTER
interface ens192
virtual_router_id 51
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass dhcp-ha-pass
}
virtual_ipaddress {
192.168.1.1/24 dev ens192
}
track_script {
chk_dhcpd
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
EOF
# 配置状态切换脚本
cat > /etc/keepalived/notify.sh << 'EOF'
#!/bin/bash
TYPE=$1
NAME=$2
STATE=$3
case $STATE in
"MASTER")
systemctl restart dhcpd
logger "Keepalived: DHCP服务切换为MASTER状态"
;;
"BACKUP")
systemctl stop dhcpd
logger "Keepalived: DHCP服务切换为BACKUP状态"
;;
"FAULT")
systemctl stop dhcpd
logger "Keepalived: DHCP服务进入FAULT状态"
;;
*)
logger "Keepalived: 未知状态 $STATE"
exit 1
;;
esac
EOF
chmod +x /etc/keepalived/notify.sh
# 启动keepalived
sudo systemctl enable --now keepalived
🔄 切换逻辑:
chk_dhcpd 脚本每 2 秒检查 dhcpd 进程是否存在,失败 2 次即触发降级 notify.sh 在 MASTER 状态下 restart dhcpd,确保租约文件最新;BACKUP 下 stop dhcpd,避免双主冲突
6.3 监控指标与告警规则

此表应作为 Prometheus + Grafana 面板的数据源,或集成至 技术文档 中的避坑指南章节。
6.4 版本控制与配置管理
使用 Git 对 DHCP 配置实施全生命周期管理:
# 使用Git进行配置管理
sudo dnf install git -y
# 初始化配置仓库
sudo mkdir -p /etc/dhcp/.git
cd /etc/dhcp
sudo git init
sudo git config user.email "dhcp-admin@corp.example.com"
sudo git config user.name "DHCP Admin"
# 创建.gitignore
cat > .gitignore << 'EOF'
# 忽略租约文件
dhcpd.leases
dhcpd.leases~
# 忽略备份文件
*.bak
*.backup
# 忽略临时文件
*.tmp
*.temp
EOF
# 初始提交
sudo git add .
sudo git commit -m "Initial DHCP configuration"
# 创建部署钩子
cat > .git/hooks/post-commit << 'EOF'
#!/bin/bash
# 提交后自动检查配置并重启服务
if dhcpd -t -cf /etc/dhcp/dhcpd.conf; then
systemctl reload dhcpd
logger "DHCP配置已更新并重新加载"
else
logger "DHCP配置检查失败,服务未重启"
exit 1
fi
EOF
chmod +x .git/hooks/post-commit
📜 此方案实现:
- 每次
git commit 自动触发 dhcpd -t 语法校验 + systemctl reload
- 所有配置变更留痕,
git blame 可追溯责任人与时间
- 与 运维 & 测试 板块的 CI/CD 流水线天然契合
6.5 总结检查清单
# openEuler 24.03 DHCP部署检查清单
## 环境准备
- [ ] 系统已更新至最新版本
- [ ] 网络接口配置为静态IP
- [ ] 防火墙和SELinux策略已规划
- [ ] 存储空间充足(>10GB可用空间)
## 服务安装
- [ ] ISC DHCP服务器已安装
- [ ] 配置文件语法已验证
- [ ] 服务监听接口已配置
- [ ] systemd服务单元已优化
## 网络配置
- [ ] IP地址规划已完成
- [ ] 子网和地址池定义正确
- [ ] 静态绑定配置完整
- [ ] DNS、网关等选项配置正确
## 安全配置
- [ ] 防火墙规则已配置
- [ ] SELinux策略已调整
- [ ] 文件权限设置正确
- [ ] 访问控制策略已定义
## 监控运维
- [ ] 监控脚本已部署
- [ ] 日志轮转已配置
- [ ] 备份策略已实施
- [ ] 告警规则已定义
## 性能优化
- [ ] 系统内核参数已优化
- [ ] DHCP进程资源限制已设置
- [ ] 数据库维护计划已安排
- [ ] 网络缓冲区已调整
## 高可用性
- [ ] 备份方案已制定
- [ ] 故障切换机制已测试
- [ ] 数据同步策略已定义
- [ ] 恢复流程已文档化
通过以上完整配置,您将在 openEuler 24.03 LTS 系统上建立一个企业级、高性能、安全可靠的 DHCP 服务。该方案不仅提供了基础的功能实现,还涵盖了监控、安全、高可用等生产环境所需的各个方面。
关键优势:
- 深度集成 openEuler 特性:充分利用发行版的先进功能
- 模块化配置:便于维护和扩展
- 全面监控:实时掌握服务状态
- 自动运维:减少人工干预,提高可靠性
- 安全加固:多重防护确保服务安全
根据实际环境调整配置参数,定期审查和更新安全策略,您的 DHCP 服务将能够稳定支撑企业网络运行。